Attack surface management techniques
Computer Science
Another Computer Science Courses
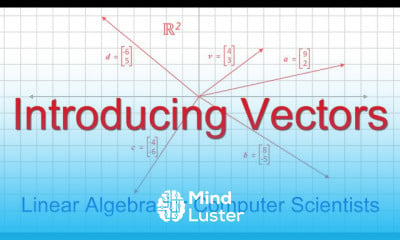
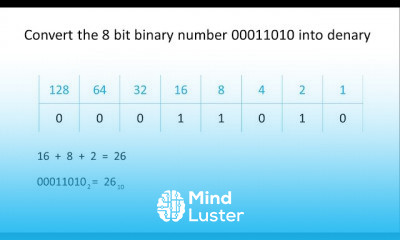
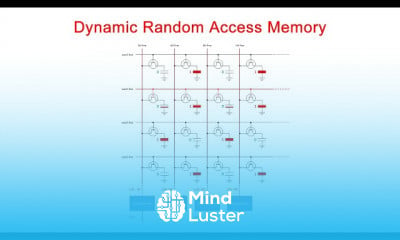
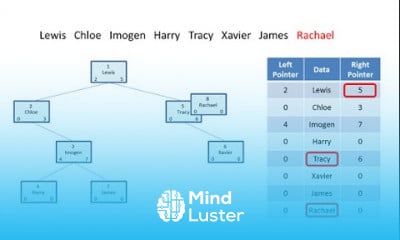
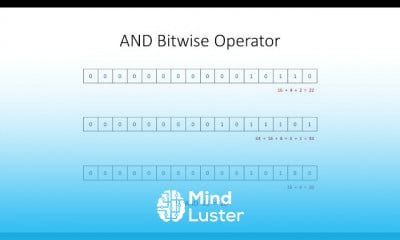
Attack surface management course, in this course involves identifying, assessing, and mitigating potential vulnerabilities and entry points that attackers could exploit to infiltrate an organization's systems or infrastructure. Through comprehensive modules, participants gain insights into various ASM methodologies, including vulnerability assessment, network and application analysis, threat monitoring, and risk prioritization. Additionally, the course explores techniques for continuous ASM to adapt to evolving cyber threats effectively. By mastering ASM principles and best practices, participants will be equipped to fortify their organization's security posture, mitigate risks, and safeguard critical assets against cyber threats. Join us to acquire essential skills and knowledge in ASM for robust cybersecurity defense.