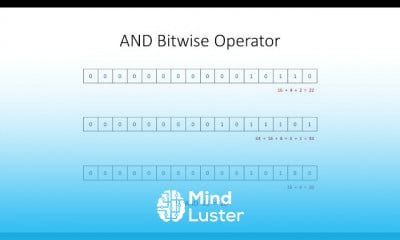
34 Methods To Define Security Requirements In S L As Security Provisions ISACA CISM DOMAIN 5
Share your inquiries now with community members
Click Here
Sign up Now
Lessons List | 339
Lesson
Show More
Lessons
Comments
Related Courses in Computer Science
Course Description
CISM ISACA COMPLETE course provides comprehensive training on the Certified Information Security Manager (CISM) certification. Explore key domains of information security management, risk assessment, incident response, and governance. Gain expertise in developing and managing information security programs aligned with organizational goals. Learn best practices, industry standards, and strategies to protect critical information assets. Join this course to master CISM concepts, enhance your career prospects, and contribute to effective information security governance in organizations. TUTORIAL
Trends
Learning English Speaking
MS Excel
Python programming language
Web Design for Beginners
Excel Course Basic to Advanced
Communication Skills
English Language
Content Marketing
Photo Editing
French
IELTS exam english
Formation efficace à l écoute de l
Every Photoshop
English Grammar for Beginners
Basic english grammar
Magento Formation Français
Excel Power Query in excel for beginners
Marketing digital
Digital Marketing Beginners
AI design tools in graphic design
Recent
Laravel 12 react crud
Laravel vuejs 2025
IELTS exam english
Business english vocabulary and idioms
Improve english vocabulary
Basic english grammar
Confusing english verbs
Prepositions in english
English tenses
Essential english phrasal verbs
British english grammar for beginners
Essential english idioms
British accents for beginners
English british pronunciation practice
British phrasal verbs
Essential business english phrases
British english pronunciation
English phrasal verbs
English alphabet pronunciation
English british traditions