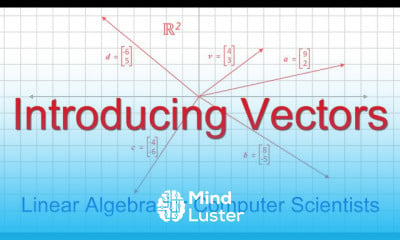
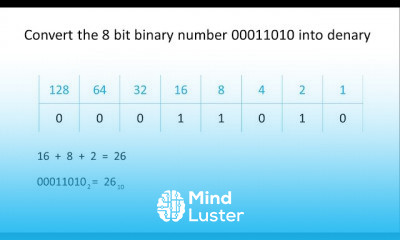
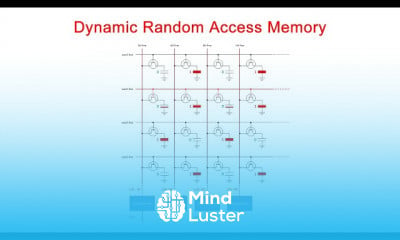
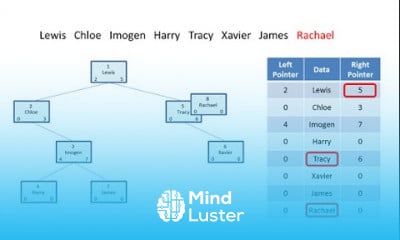
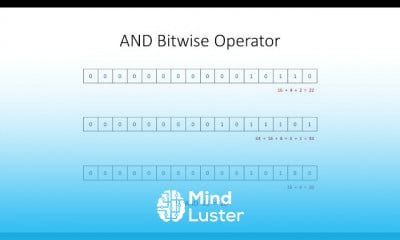
What is a Pass the Hash Attack PtH | Pass the hash PtH attacks How they work
Share your inquiries now with community members
Click Here
Sign up Now
Lesson extensions
Lessons List | 7
Lesson
Comments
Related Courses in Computer Science
Course Description
PsExec Essentials course,
in this course n this course, we'll delve into PsExec, exploring its powerful features for remote Windows management.
Trends
Graphic design tools for beginners
Artificial intelligence essentials
MS Excel
E commerce facebook Ad techniques
Facebook Ads
YouTube Earning for Beginners
Microsoft excel for accounting and finance
Essential english phrasal verbs
Excel skills for math and science
Python In 4 hours
AZ 500 Exam Cram
Figma for UX UI design
French
Becoming a product manager in 2024
Music
Hypoglycemia basics
Digital Marketing in Arabic
Table formatting in excel for beginners
Layout Android
Passive Income
Recent
Growing vegetable garden
Growing melon cantaloupe
Growing white radish
Growing and harvesting kohlrabi
Beanuts farming
Growing onions
Growing celery
Growing Harvest bean sprouts
Growing chili peppers
Growing peanuts
Growing winged beans
Growing gourds
Growing dragon beans
Harvesting guava fruit gardens
Growing pumpkins
Cabbage farming for beginners
Weeds management in carrots farming
Onion farming for beginners
Dairy farming in kenya
Maize farming for beginners